- Edited
Hi All,
In the recent days I noticed this in my logs file.
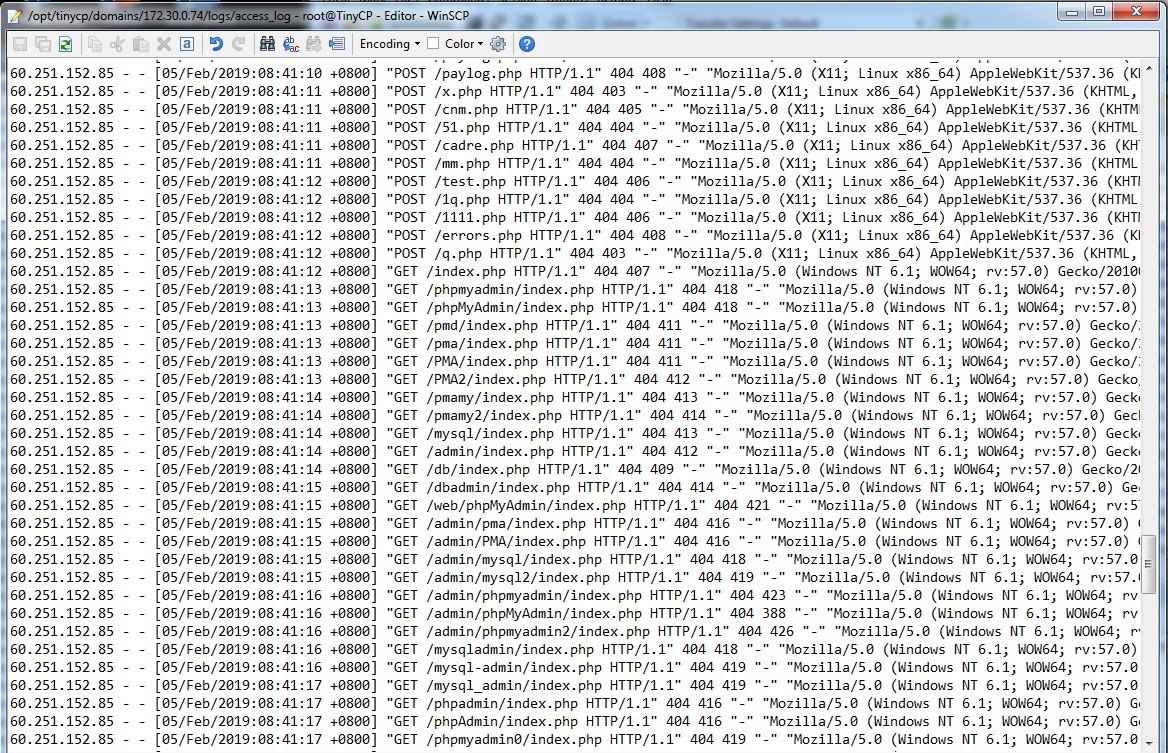
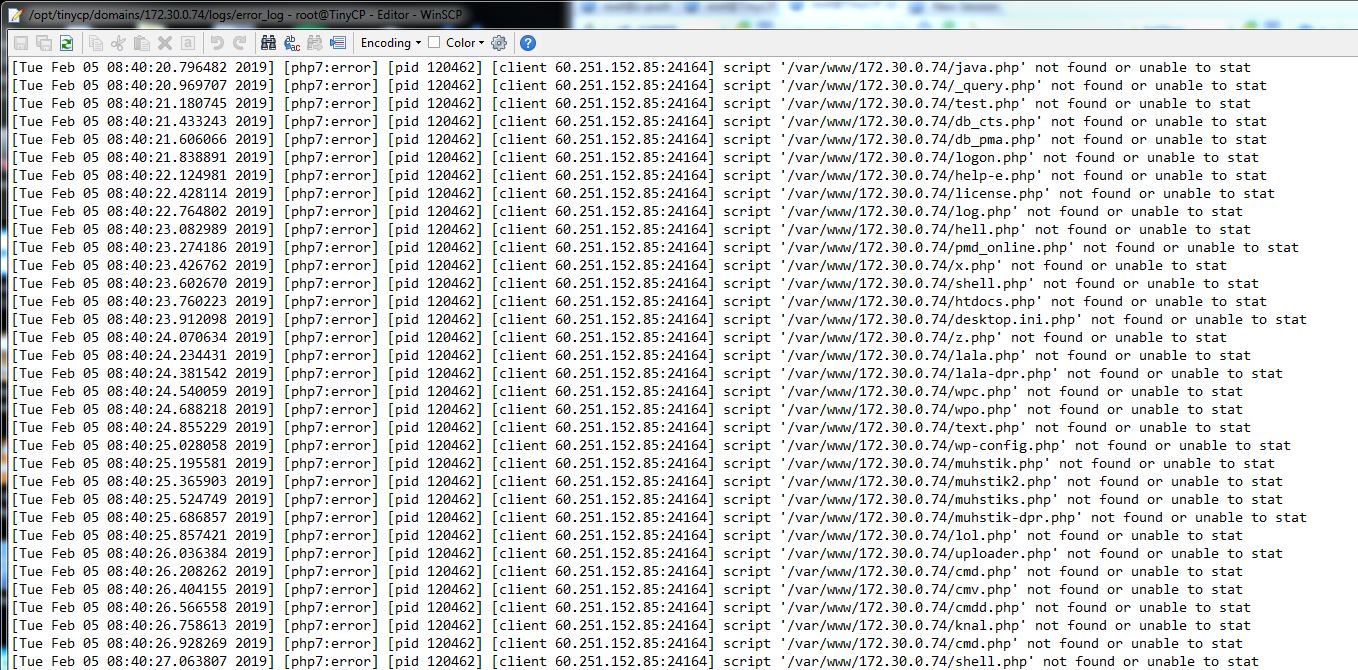
Of course I want to exposed malicious IP 60.251.152.85 and so forth but I noticed this "scumbag" would not stop anytime soon, so I came up with following solution:
Add/edit /etc/fail2ban/filter.dapache-antibot.conf
# change badurls to fit your taste and needs, this are the more common ones
[Definition]
badurls = myadmin|phpadmin|sql|webdb|wp-login\.php|soapCaller|manager|setup\.php|pma|status|admin\.php|phpmyadmin\.php|pma\.php|PMA|phpmyadmin|myadmin|mysql|mysqladmin|sqladmin|mypma|admin|xampp|mysqldb|mydb|db|pmadb|phpmyadmin1|phpmyadmin2|administrator|database|sql|phpMyAdmin|MyAdmin|dbadmin|php-myadmin|phpmy-admin|phpmyAdmin
failregex = ^(?i)<HOST> .* "(GET|POST|HEAD) .*(%(badurls)s).* HTTP.*" (403|404) .*$
^(?i)<HOST> .* "(GET|POST|HEAD) / HTTP.*" (403|404) .*$
ignoreregex =
Add/edit /etc/fail2ban/jail.conf

NOTE: * in the logpath includes all domains within tinycp hence if "60.251.152.85" changes to a different domain, it will still get denied access to server.
The above filter plus existing recidive.conf will eradicate the scumbag
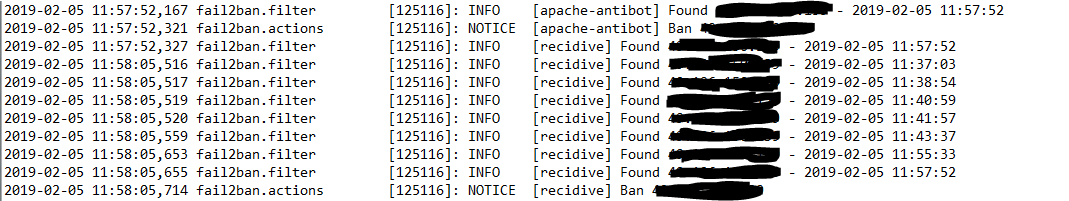
Hope this help someone out there.
Regards
